Welcome, dear readers, to a discussion on enhancing cloud security posture to create a safe and secure environment for your digital assets. As more and more businesses rely on cloud technology for storage, communication, and operations, it is crucial to prioritize cybersecurity measures. By implementing effective strategies and staying updated on the latest threats, organizations can mitigate risks and protect sensitive information from cyberattacks. Let’s explore some key steps to strengthen your cloud security posture and safeguard your data.
Importance of Cloud Security Posture
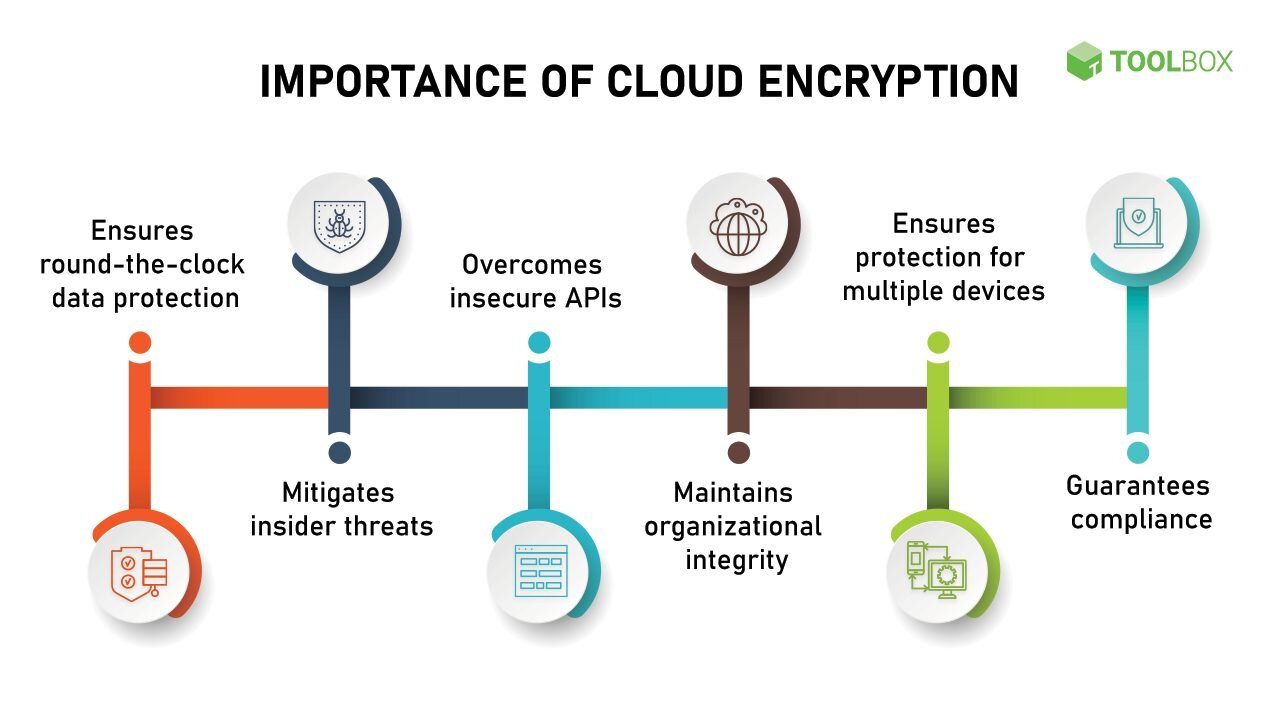
Cloud security posture refers to the overall security status of an organization’s cloud infrastructure. It encompasses all the security protocols, controls, and measures put in place to protect data, applications, and systems on the cloud. Having a strong cloud security posture is crucial for any organization that utilizes cloud services, as it helps mitigate the risks associated with cyber threats, data breaches, and unauthorized access.
One of the main reasons why cloud security posture is important is the growing number of cyber threats targeting cloud-based systems. As more organizations transition to the cloud for their operations, cybercriminals are increasingly targeting cloud environments to steal sensitive information or disrupt services. Without a strong security posture in place, organizations are vulnerable to a wide range of threats, including malware infections, phishing attacks, and data breaches. By prioritizing cloud security posture, organizations can better protect their digital assets and reduce the risk of falling victim to cyber attacks.
Another key reason for emphasizing cloud security posture is the need to comply with regulatory requirements and industry standards. Many industries have strict regulations governing the protection of sensitive data, such as the Health Insurance Portability and Accountability Act (HIPAA) for healthcare organizations or the General Data Protection Regulation (GDPR) for companies operating in the European Union. Failure to comply with these regulations can result in severe financial penalties and damage to the organization’s reputation. Implementing a robust cloud security posture can help organizations meet these compliance requirements and avoid costly fines.
Additionally, maintaining a strong cloud security posture is essential for safeguarding customer trust and loyalty. In today’s digital age, consumers are more aware of the risks associated with data breaches and privacy violations. They expect organizations to take the necessary precautions to protect their personal information and ensure the security of their online transactions. By demonstrating a commitment to cloud security through a well-defined security posture, organizations can build trust with their customers and differentiate themselves from competitors who may not prioritize security.
Furthermore, having a strong cloud security posture can help organizations proactively identify and address security vulnerabilities before they are exploited by malicious actors. By conducting regular security assessments, implementing proactive monitoring tools, and staying informed about emerging threats, organizations can stay one step ahead of cyber attackers and minimize the impact of potential security incidents. This proactive approach to security not only enhances the organization’s overall security posture but also helps mitigate the potential financial and reputational damage that can result from a security breach.
In conclusion, the importance of cloud security posture cannot be overstated in today’s digital landscape. Organizations must prioritize security measures to protect their cloud environments from cyber threats, comply with regulatory requirements, build customer trust, and proactively mitigate security risks. By investing in a strong cloud security posture, organizations can ensure the confidentiality, integrity, and availability of their data and systems on the cloud, ultimately safeguarding their operations and reputation in an increasingly interconnected world.
Best Practices for Enhancing Cloud Security Posture
When it comes to enhancing the security posture of your organization’s cloud environment, there are several best practices that can help protect your data and assets from potential threats. One of the most important steps is to implement a multi-layered security approach that includes encryption, access controls, and monitoring tools. Encryption is essential for protecting data both at rest and in transit, while access controls help ensure that only authorized users can access sensitive information.
Another key best practice is to regularly update and patch your cloud infrastructure. Vulnerabilities in software and applications can be exploited by hackers to gain access to your systems, so it’s important to stay on top of security updates. In addition, implementing strong password policies and multi-factor authentication can help prevent unauthorized access to your cloud environment.
Regularly auditing and monitoring your cloud environment is also crucial for enhancing security posture. By closely monitoring for any unusual activity or unauthorized access attempts, you can quickly identify and address potential threats before they escalate. This includes monitoring log files, network traffic, and user activity to identify any potential security incidents.
Training your employees on best practices for cloud security is another important step in enhancing your organization’s security posture. Many security breaches are the result of human error, so it’s essential to educate your staff on how to recognize phishing attempts, avoid downloading malicious software, and follow proper security protocols. By making security awareness training a priority, you can help reduce the risk of insider threats and improve overall security.
Lastly, it’s important to have a response plan in place in the event of a security incident. This includes having a designated incident response team, conducting regular security drills, and establishing communication protocols for notifying employees and stakeholders of a breach. By being prepared to respond quickly and effectively to security incidents, you can minimize the impact on your organization’s operations and reputation.
Common Threats to Cloud Security Posture
Cloud security posture refers to the overall security of an organization’s cloud environment, including its infrastructure, applications, data, and users. While the cloud offers many benefits, such as scalability and flexibility, it also presents unique security challenges. Here are some common threats to cloud security posture:
1. Data Breaches: One of the most significant threats to cloud security posture is data breaches. Cybercriminals may target cloud environments to steal sensitive data, such as customer information, intellectual property, and financial records. Data breaches can have serious consequences for organizations, including financial losses, damage to reputation, and legal repercussions. To mitigate the risk of data breaches, organizations should implement robust encryption, access controls, and monitoring solutions in their cloud environment.
2. Account Hijacking: Account hijacking occurs when cybercriminals gain unauthorized access to a user’s cloud account. Once inside the account, attackers can steal data, disrupt services, and launch further attacks within the cloud environment. To prevent account hijacking, organizations should enforce strong authentication mechanisms, such as multi-factor authentication, and regularly monitor user activity for any signs of suspicious behavior.
3. Insider Threats: While external threats often get the most attention, insider threats pose a significant risk to cloud security posture. Insiders, such as employees, contractors, or business partners, may intentionally or unintentionally compromise the security of the cloud environment. They could leak sensitive data, misuse access privileges, or introduce malware into the system. Organizations should conduct regular security training for employees, implement least privilege access controls, and monitor user activity to detect and prevent insider threats.
4. DDoS Attacks: Distributed Denial of Service (DDoS) attacks are another common threat to cloud security posture. In a DDoS attack, cybercriminals flood a cloud service with a large volume of traffic, overwhelming its resources and causing disruption to legitimate users. To defend against DDoS attacks, organizations should deploy DDoS mitigation solutions, such as rate limiting, traffic filtering, and traffic diversion, to protect their cloud environment from being taken down by malicious actors.
5. Compliance Violations: Compliance violations can also pose a threat to cloud security posture, especially for organizations in regulated industries, such as finance, healthcare, and government. Failure to comply with industry regulations, such as GDPR, HIPAA, or SOX, can result in hefty fines, legal liabilities, and reputational damage. To avoid compliance violations, organizations should ensure that their cloud environment meets industry standards and regularly audit their security controls to maintain compliance.
In conclusion, maintaining a strong cloud security posture requires organizations to be vigilant against a variety of threats, ranging from data breaches and account hijacking to insider threats and DDoS attacks. By implementing robust security measures, conducting regular security audits, and staying abreast of the latest security trends, organizations can better protect their cloud environment and safeguard their sensitive data.
How to Assess and Improve Your Cloud Security Posture
Assessing and improving your cloud security posture is vital to ensuring the safety and integrity of your data in the cloud. Here are some key steps to consider:
1. Conduct a Security Audit: Start by conducting a thorough security audit of your cloud environment. This involves assessing the current state of your security measures, identifying any vulnerabilities or weaknesses, and determining what areas need improvement. By conducting a security audit, you can gain a better understanding of your cloud security posture and make informed decisions on how to enhance it.
2. Implement Access Controls: One of the most important aspects of cloud security is controlling who has access to your data and resources. Implementing access controls such as strong authentication mechanisms, role-based access control, and least privilege principles can help minimize the risk of unauthorized access and data breaches. Regularly reviewing and updating access controls is also essential in maintaining a secure cloud environment.
3. Encrypt Data: Encrypting your data is another crucial step in enhancing your cloud security posture. By encrypting sensitive data both at rest and in transit, you can protect it from unauthorized access and ensure its confidentiality. Utilize strong encryption algorithms and key management practices to safeguard your data and comply with industry regulations and standards.
4. Regularly Monitor and Analyze Security Events: Monitoring and analyzing security events in your cloud environment are essential for detecting and responding to potential security threats. Implementing a robust security monitoring solution that tracks and records all activities within your cloud infrastructure can help you identify suspicious behavior, unusual patterns, or unauthorized access attempts. By monitoring security events in real-time and analyzing log data, you can proactively address security incidents and prevent data breaches.
Furthermore, consider implementing security information and event management (SIEM) tools that provide comprehensive visibility into your cloud infrastructure and enable you to correlate and analyze security events across multiple sources. SIEM solutions can help streamline threat detection and response processes, improve incident response times, and enhance overall security posture.
5. Perform Regular Security Assessments and Penetration Testing: Regularly assessing your cloud security posture through security assessments and penetration testing can help identify weaknesses and vulnerabilities that may be exploited by attackers. Conducting periodic security assessments and penetration tests allows you to proactively identify and address security gaps, prioritize remediation efforts, and ensure that your cloud environment remains secure against evolving threats.
By following these steps and incorporating best practices in cloud security, you can assess and improve your cloud security posture to better protect your data, applications, and infrastructure from cyber threats and breaches.
Tools and Technologies for Monitoring Cloud Security Posture
When it comes to monitoring the security posture of your cloud environment, there are a variety of tools and technologies available to help ensure that your data is protected and secure. These tools can help you detect any vulnerabilities or breaches in real-time, allowing you to take immediate action to mitigate any potential risks.
One popular tool for monitoring cloud security posture is Cloud Security Posture Management (CSPM) platforms. These platforms provide a centralized dashboard where you can view the security status of your cloud resources, including any misconfigurations or compliance violations. CSPM tools can also automate security checks and provide recommendations for remediation, making it easier to maintain a strong security posture.
Another essential technology for monitoring cloud security posture is Cloud Access Security Brokers (CASBs). CASBs act as a security control point between your organization’s on-premises infrastructure and cloud provider’s infrastructure. They allow you to monitor and enforce security policies for data in the cloud, providing visibility into user activity and data usage. CASBs also offer threat protection, data loss prevention, and encryption to protect your sensitive information.
One more critical tool for monitoring cloud security posture is Security Information and Event Management (SIEM) systems. SIEM systems collect and analyze security data from various sources, including cloud environments, to detect and respond to security incidents. By correlating data and detecting patterns of behavior, SIEM tools can help you identify potential security threats and take action to prevent attacks proactively.
Additionally, cloud-native security tools such as Amazon Web Services (AWS) Config and Azure Security Center can provide you with insights into the security configuration of your cloud resources. These tools can help you assess security risk, monitor compliance, and detect potential security issues in your cloud environment.
Lastly, endpoint detection and response (EDR) solutions can also play a crucial role in monitoring cloud security posture. EDR solutions can monitor endpoint activity in your cloud environment, detect malicious behavior, and respond to security incidents in real-time. By combining EDR with other cloud security tools, you can enhance your overall security posture and protect your data from advanced threats.
Overall, using a combination of these tools and technologies can help you maintain a strong security posture in your cloud environment, ensuring that your data remains protected from potential threats and vulnerabilities.
Originally posted 2025-05-08 17:44:44.